Papyrs with Integrated Windows Authentication (IWA) using LDAP
You can connect Papyrs to a Windows network. This has a number of benefits:
- Centrally administer the users in your team using Windows Server User Management tools
- Synchronize contact information between Papyrs & Active Directory
- Single Sign-On supported. Competely automatic and passwordless login (NTLM challenge response) for everybody on the Windows network
- Bulk import users from your Windows Network
- Papyrs can connect to multiple Windows Network groups
Here you can read the details about how Papyrs with Integrated Windows Authentication works. We also have a page explaining the benefits of using a Papyrs intranet on an existing Windows network.
Papyrs uses Integrated Windows Authentication, if available. This is also known as: HTTP Negotiate Authentication, NT Authentication, NTLM Authentication, Windows Domain Authentication, and Windows NT Challenge/Response Authentication.
Papyrs LDAP is compatible with Microsoft Active Directory (AD), Microsoft Azure Active Directory (Azure AD), and Apple Open Directory, and Linux OpenLDAP.
Connecting Papyrs to your Windows Network
In order to integrate Papyrs with your Windows network a user account for Papyrs to connect to the Active Directory.| Windows Server Hostname | e.g. ad.yourcorp.com |
| LDAP Port | typically 389 or 636 |
| Base DN | e.g. CN=Users,DC=example,DC=com |
| Papyrs LDAP user | e.g. CN=papyrsldap,OU=users,DC=example,DC=com |
| Papyrs LDAP password | **** |
Navigate to https://yoursite.papyrs.com/settings/people/ldap/ and click on Set up LDAP integration to get started. You'll see a form like the one below:
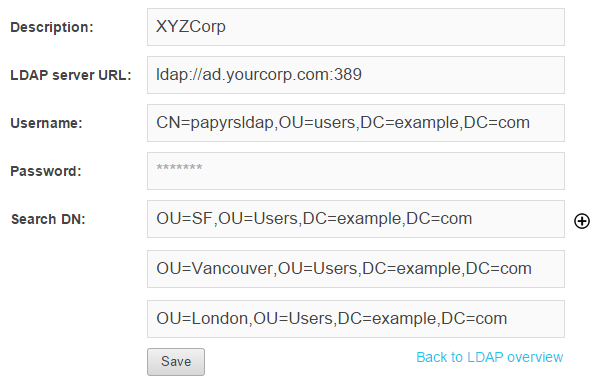
Finding the Distinguished Name of the Papyrs user account
If you're unsure what the Distinguished Name is of the Papyrs user you've added to your Windows network, you can look it up like this:
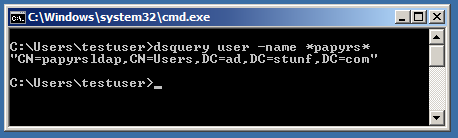
(Alternatively, you can put the user's displayName or email address in the Username field)
LDAP user and password
Add a user to the Windows Domain with sufficient permissions to retrieve a list of users in the Base Distinguished Name (Base DN). This user account is used to invite people to the Papyrs Intranet and to synchronize contact information (if desired).
Note: Papyrs doesn't need access to any other accounts on the network, nor do we require any additional access permissions. So we won't be able to access any files on the Windows network, nor will we be able to access any other classified information. We don't need access to the passwords of the users in the directory either, the user authentication will be handled by your Activity Directory server inside your network — Papyrs just gets a message from the server indicating whether the login was successful.
LDAP Port & Encryption
Papyrs supports two types of encryption for communication with the LDAP server (typically Active Directory): LDAPS and LDAP through an SSL tunnel/proxy. You can read more about configuration of LDAPS on MS Technet. Active Directory uses port 389 by default without encryption, and 636 for LDAPS.
Firewall
Papyrs will connect to the Active Directory server from ldap.papyrs.com and requires access to a single port. So the Active Directory Server doesn't need to be exposed to the entire internet and all existing firewalls can remain in place.
Testing the connectionThe next step is to verify that Papyrs can connect to the Active Directory server:
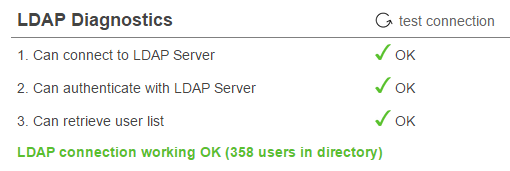
If all is well you'll see "LDAP connection working OK" like in the screenshot above. Otherwise you'll get an error of where Papyrs gets stuck. You'll see exactly at what stage the failure occurs to make the problem easy to locate. If you run into any trouble though, don't hestiate to contact us at team@papyrs.com and we'll see if we can figure out where the problem lies.
Set Active Directory Preferences
Before you invite people to your intranet you can manage your LDAP preferences:
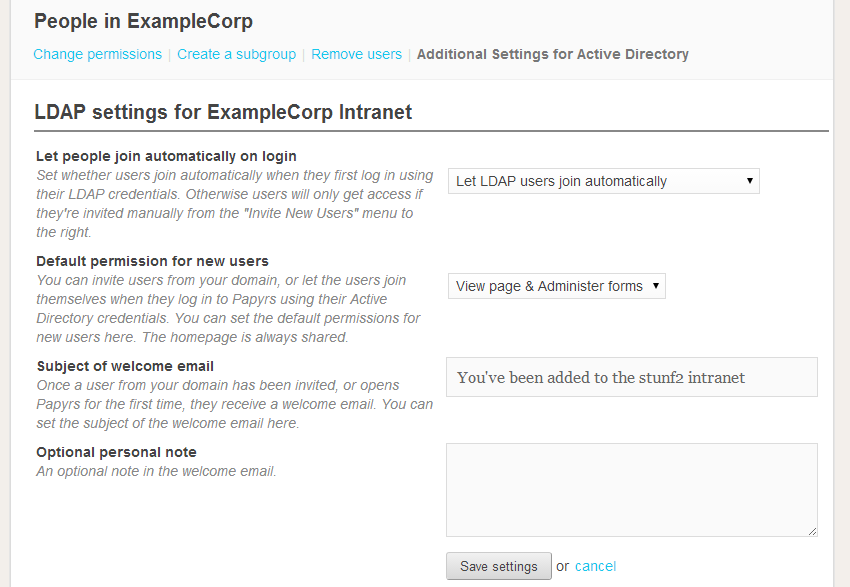
You can configure:
- Whether people can join automatically or need to be invited.
- What their default permissions will be.
- What the welcome email looks like.
Inviting users from your Windows Network
After a connection between Papyrs and your Windows network has been established inviting people takes only a couple of clicks.
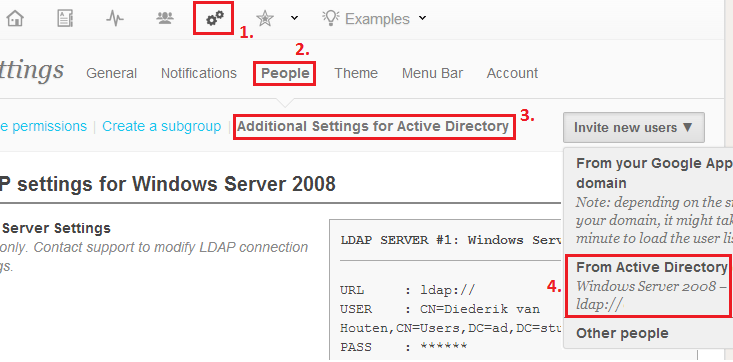
After clicking on Invite New Users > From Active Directory you'll be presented with a list of users in your Windows network:
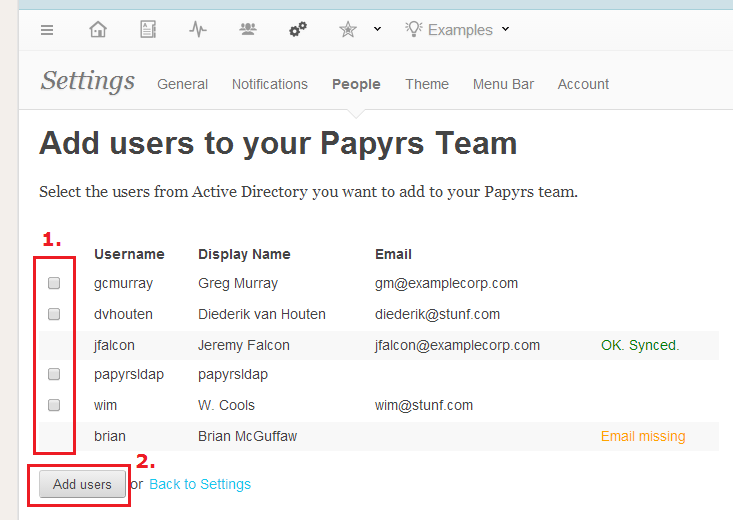
Click the checkboxes next to the users you want to invite and click "Add Users" to invite them to Papyrs. They'll receive a welcome email (with a customized invitation message) and will be able to log in right away.
Logging in
When people try to access a protected page on the intranet they'll see the following log in window:
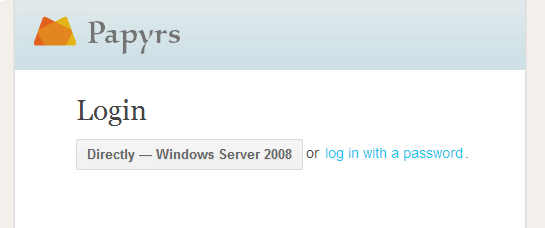
The user can then choose to log in automatically (without a username or password) from a computer that's part of your intranet. Otherwise the user can log in with their Active Directory credentials (using either their mail, sAMAccountName, userPrincipalName) and their Active Directory (Windows) password. Users will also still be able to log on using their Papyrs email address and password. The text on the login button can be customized and logins with a password can be disabled if needed. When logging on using the LDAP login button the web browser will attempt to log on using Integrated Windows Authentication (using a challenge-response system). When this doesn't work a regular password prompt will appear instead.
For Integrated Windows Authentication to work the web browser has to know that the Papyrs site is part of the Intranet Zone. For Microsoft Internet Explorer and Google Chrome websites can be added to the intranet zone manually or for people on the network using a Group Policy.
User Synchronization
Papyrs connects to the LDAP server every night to update the list of users in the Windows network. Administrators of a Papyrs account can add those users to Papyrs (or allow users to invite themselves to the Papyrs group) and contact information for these new users is pulled from the Active Directory. When users log in to Papyrs the Active Directory server is contacted to verify the user is permitted to log in, and if so access to Papyrs is granted. If needed, Papyrs can be connected to multiple active directory servers.
Questions? Not sure if Papyrs with LDAP integration is what you need? Contact us with any questions you may have.
